Websphere-oidrcp-adapter (Luna)
Your company has a business repository of employee accounts in Exchange Online MS Office 365. You want your web application users to log in using their MS Office 365 business account credentials. You want to use a single login point (Single Sign-On, SSO) in your applications that MS Office 365 provides. Implementing the Websphere-oidrcp-adapter (Luna) library is the PERFECT solution to your needs.
The goal is to launch the Single Sign-On (SSO) mechanism from MS Office 365 in your company's (organization's) local web application. The assumption is that the web application is installed on the application server IBM WebSphere Application Server. An example of implementing the solution is the login page https://bpm.umed.pl/.
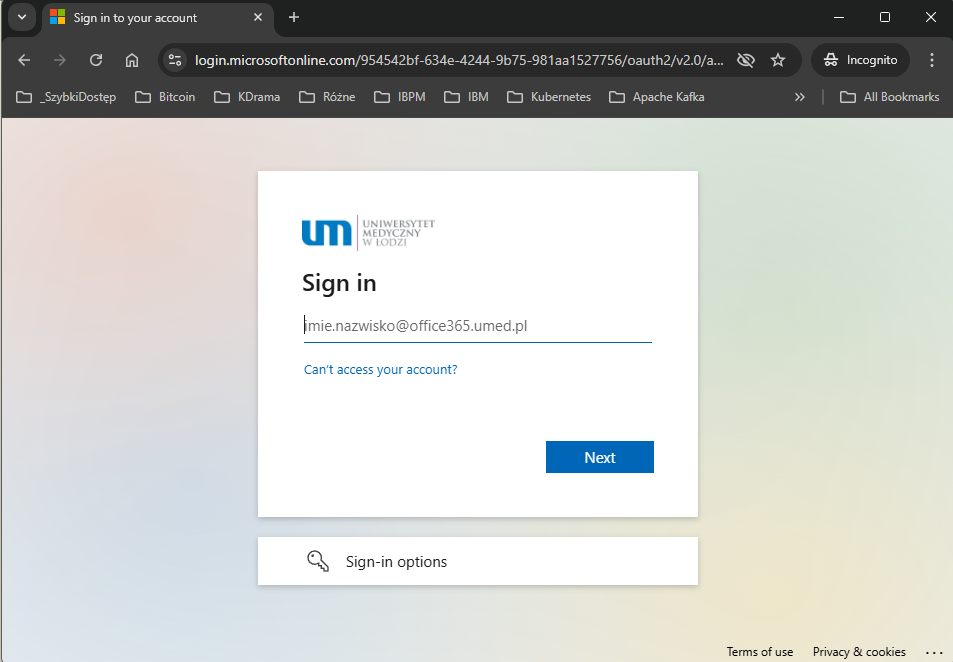
Luna is a customized implementation of the com.ibm.ws.security.oidc.client.RelyingParty class.
If you have a local LDAP user repository and user names are different than in MS Office 365, then the implemented solutions will allow you to MAPP the appropriate entry attributes with user names,
which are returned by the OpenId Connect mechanism to the attributes with user names stored in the local LDAP repository.
The mechanism uses the LDAP configuration defined in the mechanisms of federated user repositories WIM (Websphere Identity Manager, Federated repositories with WebSphere® Application Server).
The abbreviation OIDCRP stands for WebSphere OpenID Connect Relying Party.
Negotiation method operation
The assumption is that the local web application uses authentication mechanisms based on the local LDAP/AD repository.
The implementation performs the following steps:
- Running the original method from the parent class.
- Searching for a user in LDAP repositories based on the name returned by the original mechanism.
- Based on the data found in the LDAP entry, sets a new user name.
- We log in to MS Office 365 with a user named
scichy@<domain_name>. - This user name is stored in the local LDAP/AD repository in the attribute named
mail. The mechanism searches for a user in the local repository using the filter criteria(mail=scichy@<domain_name>). - The target username in the local application is stored in the local LDAP/AD repository in an attribute named
uid. For the searched user, this attribute takes the valueslawas. Therefore, the user will be logged into the application asslawas.
Starting the mechanism allows you to simultaneously use the MS Office 365 SSO authentication method and the method based on the local LDAP/AD repository used in the application, i.e. you can still use the 'BASIC', 'FORM' login methods based on the name and password from the local user repository. This allows access to the application for those users who do not have an account in MS Office 365.
Installation
The installation package is an archive containing a file named websphere-oidcrp-adapter-<version>.jar (e.g., websphere-oidcrp-adapter-9.0.8.jar). This file should be placed in the $WAS_INSTALL/lib/ext directory, e.g., /opt/IBM/BAW/20.0.0.1/lib/ext.
Configuring caches
Remember to configure caches.
Configuration path in WebSphere console: Resources > Cache instances > Object cache instances
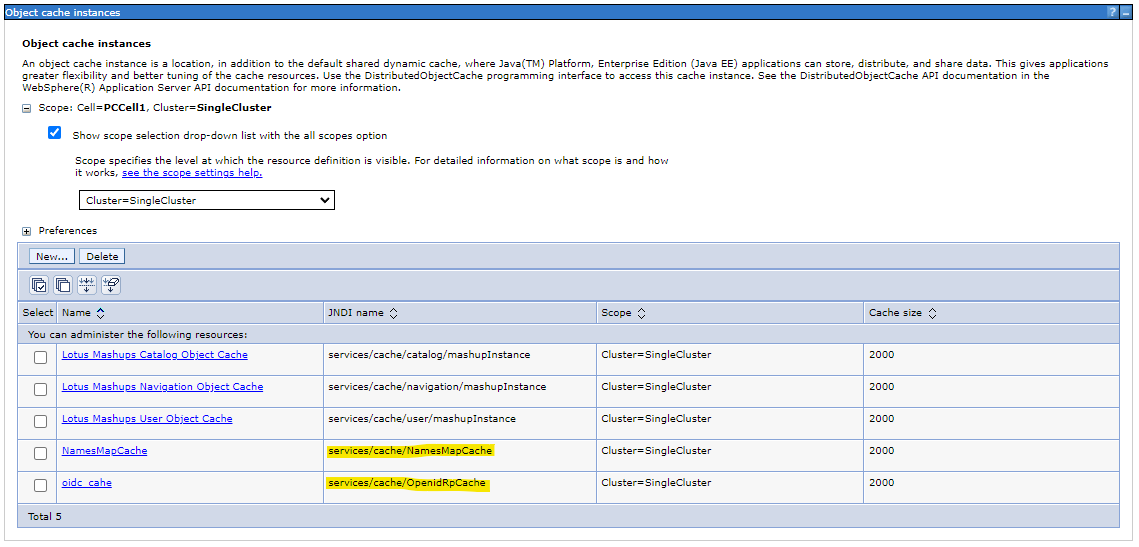
Then set the parameters accordingly:
- jndiCacheName - JNDI name of the cache, where the user's session data will be stored.
- namesMap.jndiCacheName - JNDI name of the cache, where the data related to mapping the original user name to the local name will be stored.
Sample interceptor configuration
Configuration path in WebSphere console: Global security > (Web and SIP security) > Trust association > Interceptors
We add interceptor pl.slawas.ws.security.oidc.client.RelyingParty.
The following sites are worth visiting:
- Adding an application in Azure AD for SSO with Connections
- Updating WebSphere to support Azure AD OIDC authentication for Connections
- Configuring an OpenID Connect Relying Party
- OpenID Connect Relying Party custom properties
- CWTAI2009I: The OpenID Connect relying party (RP) did not find an entry for session cookie OIDCSESSION_12345678 in the Session cache.
Below is a screenshot from the WebSphere console with an example configuration:
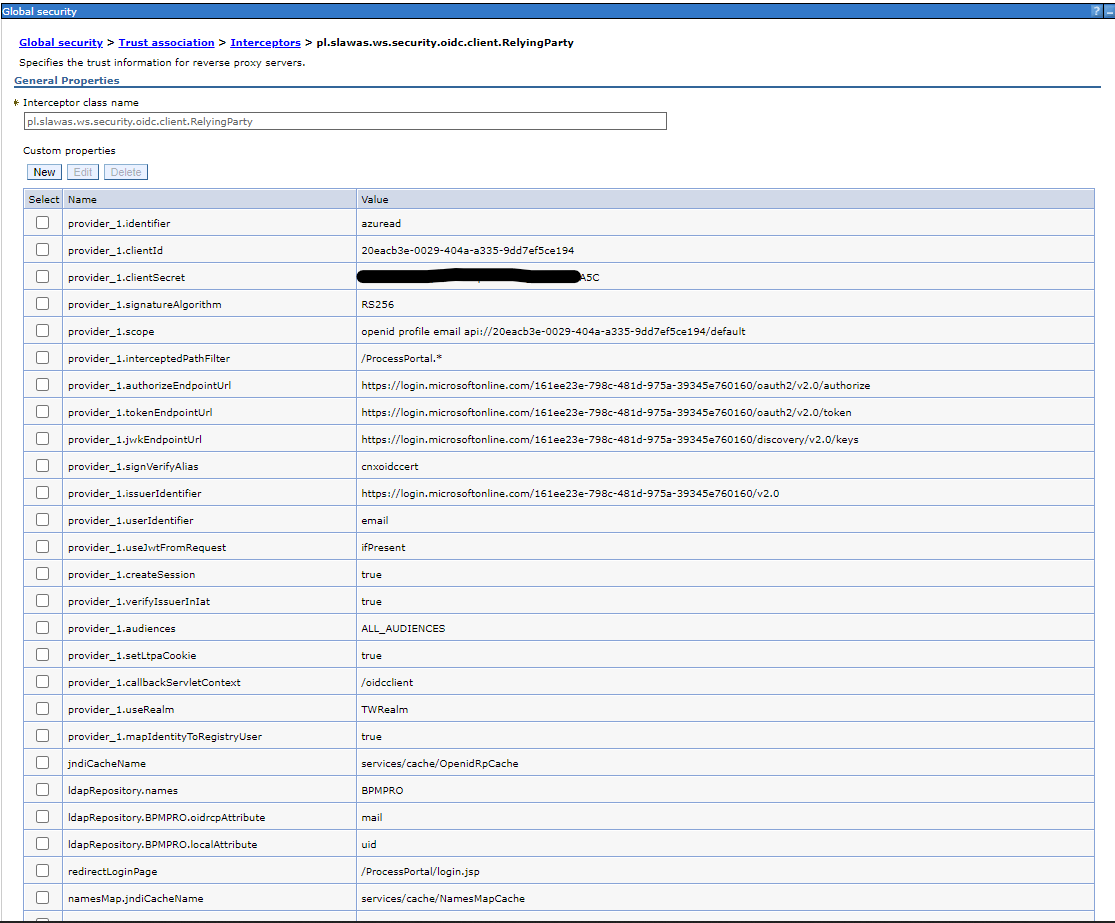
Additional parameters are available in the configuration:
- ldapRepository.names - list of federated LDAP repository names defined in the WebSphere configuration, which are to be used to search for the user entry. The names are separated by a comma.
- ldapRepository.%s.oidrcpAttribute - a parameter defining the user attribute name, which represents the user name/login returned by the external OpenID Connect system. The mapping basis. Based on this attribute and its value, the user will be searched for. In the RP configuration, the argument '%s' is replaced by the LDAP repository name and applies to the given repository. Example: ldapRepository.BPMPRO.oidrcpAttribute - where BPMPRO is the LDAP repository name.
- ldapRepository.%s.localAttribute - a parameter defining the user attribute name, which represents the user name/login returned by LDAP. The mapping basis. Based on this attribute and its value, the logged-in user name will be assigned. In the RP configuration, the argument '%s' is replaced by the LDAP repository name and applies to the given repository. Example: ldapRepository.BPMPRO.localAttribute - where BPMPRO is the LDAP repository name.
- redirectLoginPage - optional parameter - an additional parameter in the RP configuration that allows redirecting a request to a specific page after an error occurs in a given negotiation method implementation.
- namesMap.jndiCacheName - optional parameter, the JNDI name of the cache, in which data related to mapping its original name to the local name will be stored. Do not set if you want to use the local cache. However, if you want to use the dynamic cache, remember to define it beforehand!
- namesMap.maxLocalCacheSize - optional parameter, the size (entry number) of the local cache, used when defining the local cache of the user name map. If you do not set it, the default value of 2000 will be used.
- namesMap.sessionCacheCleanupFrequency - optional parameter, the lifetime of the entry in the local cache (in seconds), used when defining the local cache of the username map. If you do not set it, the default value of 1800 will be used.
- chcekUserNameByLtpaTokenURL - optional parameter, the URL to the page returning the username, in case the user is already logged in using another method. Such a page was implemented in the sample application https://github.com/SciSoftwareSlawomirCichy/defaultapplication, which must be installed beforehand. Sample URL:
https://localhost:9443/default/pages/username.jsp.
Global security - additional parameters
Configuration path in WebSphere console: Global security > Custom properties
Set global parameters:
com.ibm.websphere.security.DeferTAItoSSO=com.ibm.ws.security.spnego.TrustAssociationInterceptorImplcom.ibm.websphere.security.InvokeTAIbeforeSSO=pl.slawas.websphere.oidrcp.client.RelyingPartycom.ibm.websphere.security.disableGetTokenFromMBean=false
Setting the logout mechanism in IBM BAW/BPM
You need to set the logout mechanism to the path https://login.microsoftonline.com/common/oauth2/logout?post_logout_redirect_uri=<URL_IBM_BPM_PORTAL>&client_id=<CLIENT_ID> e.g., https://login.microsoftonline.com/common/oauth2/logout?post_logout_redirect_uri=https%3A%2F%2Fbpmbaw20test.hgdb.org%3A9443%2FProcessPortal%2F&client_id=20eacb3e-0029-404a-a335-9dd7ef5ce194.
To do this, execute the following commands:
./wsadmin.sh -conntype NONE -lang jython
path='/ServerCluster:SingleCluster/BPMClusterConfigExtension:/BPMPortal:/'
object=AdminConfig.getid(path)
clp='customLogoutPage'
print AdminConfig.showAttribute(object,clp)
AdminConfig.modify(object,[[clp,'https://login.microsoftonline.com/common/oauth2/logout?post_logout_redirect_uri=https%3A%2F%2Fbpmbaw20test.hgdb.org%3A9443%2FProcessPortal%2F&client_id=20eacb3e-0029-404a-a335-9dd7ef5ce194']])
print AdminConfig.showAttribute(object,clp)
AdminConfig.save()
Source: Configuring third-party authentication products
Support
In case of problems, please contact me by e-mail at info@scisoftware.pl. In the subject of the message, please include the prefix: [Websphere-oidrcp-adapter].
Companies that have already used the product